Call centers are a rich source of sensitive personal information, particularly financial information such as credit card details. They are the main channel where customer problems are addressed, and sensitive data are shared. Personal data such as credit card numbers and social security numbers hold great financial value and are often bought and sold on the dark web by cyber criminals.
Due to these characteristics of call centers, they are constantly exposed to both internal and external data security threats. Cyber attacks can lead to stolen call recordings, listening to calls in real time, and illegal sales of call recordings by call center agents are all examples of threats for call centers.
While tackling all these various threats necessitates robust organizational measures, staff-training, and a shift in company culture, implementing technological solutions also plays a vital role in preventing threats. Compliance with PCI standards and privacy laws present challenges to call centers as well.
In this article, we will address how VoiceBase’s automated data redaction technology can effectively address security threats and also help organizations achieve compliance with PCI standards and Privacy Laws such as GDPR.
WHY CALL CENTERS HAVE BECOME THE MAIN ATTACK SURFACE FOR FRAUDSTERS AND HACKERS
Just as businesses constantly enhance their IT security to prevent cyber-attacks and guard their digital assets, hackers and fraudsters are also improvising and finding new paths to illegally obtain data and infiltrate systems. Recently, these malicious third parties’ main target has become call centers which handle a large volume of personal data such as card numbers, social security numbers, and birthdates. According to a survey published by TRUSTID, 51% of respondents working in the Financial Services Industry identified call centers as the main channel for account-take-over attacks.
There are a few reasons for the rise in the number of attacks against call centers:
- Human involvement brings extra vulnerability: Call center agents and customer representatives have access to highly sensitive personal data such as credit card numbers. They can copy such data by taking notes during the call, copy files containing recordings or transcripts onto portable devices to sell to malicious third parties, or disclose these data to tarnish the reputation of a business for vengeance. Humans are also vulnerable to social engineering as they can be deceived into granting access to unauthorized fraudsters.
According to the TRUSTID survey, 30% of call center agents reported having access to customers’ payment card information on file even when they’re not on the phone with the customer.
- IVRs: As customer service becomes more digitized and provided online, virtual calls gained popularity. COVID also led to an 800% increase in the volume of calls. Fraudsters increasingly target this channel because it enables them to get as much information about an account as possible and also gain access to a customer account by learning the password.
- The allure of sensitive information: When a customer makes a call, they often look for a solution to a specific problem or to be informed about a specific topic. Identity authentication is thus an essential element of calls and sensitive information such as social security and credit card number are contained in those calls. Cybercriminals are attracted to call centers because of the financial incentives–Such sensitive data is highly valuable on the dark market.
MAIN DATA SECURITY THREATS FACING CALL CENTERS
Denial of Service Attacks
This type of attack refers to hackers who overwhelm the call center resources by making an excessive number of calls at the same time so the service is no longer available to those who genuinely need it. The main aims of hackers are either to distract the call centers from another hacking attack, or request ransomware payment in exchange for ending the attack.
Hacking and data breaches
Call recordings and their transcripts often contain financially valuable sensitive data that appeal to hackers. Whether it is for a legal requirement or training purposes, call centers retain call recordings and their transcripts on servers that can fall victim to a data breach.
Hackers who illegally obtain these data from call recordings and transcripts sell them on the dark web. Card details, names, date of birth, and social security numbers are stolen by these attacks and there is a strong demand on the dark market for such sensitive data.
Buyers are usually identity thieves or fraudsters who will use these personal data to conduct account-take-over (ATO) and social engineering so they can trick call centers into thinking they are the authentic customers. In a way, hacking of call recordings may lead to more ATO and social engineering attacks.
For example, Teletext Holidays company has left 212,000 audio files on an insecure Amazon server and these files contained sensitive information such as credit card details. Customers were recorded talking their card information, names, birthdates and holiday plans out loud.
Social Engineering
Call center agents have access to vast amounts of sensitive information that fraudsters attempt to convince them to disclose such information.
Social engineering in a call center environment refers to fraudulent calls aiming to manipulate or deceive call center agents into grant fraudsters access to accounts. Fraudsters already have a limited amount of information on the genuine customer such as the name and expiry date of the card. Fraudsters may have obtained such basic information on the dark market from the hackers. By using those basic information, fraudsters pose as genuine account owners to call center agents and manipulate them to gain access to accounts, transfer money or obtain more personal information and sell it.
Insider Threats
The human element in the call center environment amplifies security risks because call center agents can be bribed, threatened, or act carelessly and cause a data breach.
High turnover of call center agents, 30-45% in 2019, inevitably means less loyalty so agents are more inclined to steal customer data and profit off it.
Call center agents can also be threatened by criminals to share sensitive data.
A data breach may also result from a lack of security awareness and carelessness. Inexperienced agents may easily fall prey to fraudulent calls and provide unauthorized access to accounts.
The growing popularity of work-from-home culture also exacerbates security risks because monitoring agents is a challenge and vulnerabilities of personal devices may end up causing data leakage.
COMPLIANCE AND CALL CENTERS
Two major compliance concerns facing call centers are PCI compliance and Privacy Laws.
PCI COMPLIANCE
Any merchant that processes payment via credit or debit card payment, PCI Security Standards Council. These rules make a distinction between ‘Sensitive Authentication Data’ and ‘Card Holder Data’. ‘Sensitive Authentication Data’ includes CVC code, PIN, and magnetic stripe data that is used to authenticate customers and these cannot be stored.
The second category, ‘Cardholder Data’ includes customer name, account number, and expiration date and these can be stored by merchants. However, strong security measures such as encryption must be implemented.
If PCI is violated, PCI founders, including VISA and MasterCard, will execute specified penalties on violating parties.
PRIVACY LAW COMPLIANCE
EU’s GDPR and US Federal Privacy Laws apply to personally identifiable information and data such as credit card numbers, CVC code, and expiry date fall under this category.
British Airways was fined £20 million by the UK Data Protection Authority because it could not prevent unauthorized access to payment card information of approximately 400,000 individuals.
In the US, financial personal information is not subject to CCPA but rather regulated by federal financial privacy laws such as the Bank Secrecy Act and Gramm-Leach-Bliley Act. For example, Equifax agreed to pay 575$ million to FTC because of the compromise of sensitive financial data under the latter privacy law.
HOW DATA REDACTION AIDS COMPLIANCE WITH BOTH PCI AND PRIVACY LAWS
PCI requires that sensitive authentication data should not be stored. Therefore, even the storage of CVC code or magnetic stripe data in encrypted form in a secure space is prohibited. Redaction technology helps businesses comply with this requirement as it detects such data and strips it off the records immediately before it is even stored.
Sensitive data redaction helps comply with GDPR. GDPR article 5 states that you must take appropriate measures to ensure security and integrity of personal data and you must prevent unauthorized access, loss or destruction of personal data. Data redaction eliminates the risk of unauthorized access or loss because sensitive data is removed from the records. GDPR requires that security measures should be appropriate to the data at hand and using highly effective redaction technology is a proportionate measure for protection of sensitive data.
VOICEBASE PCI REDACTION ACHIEVES COMPLIANCE
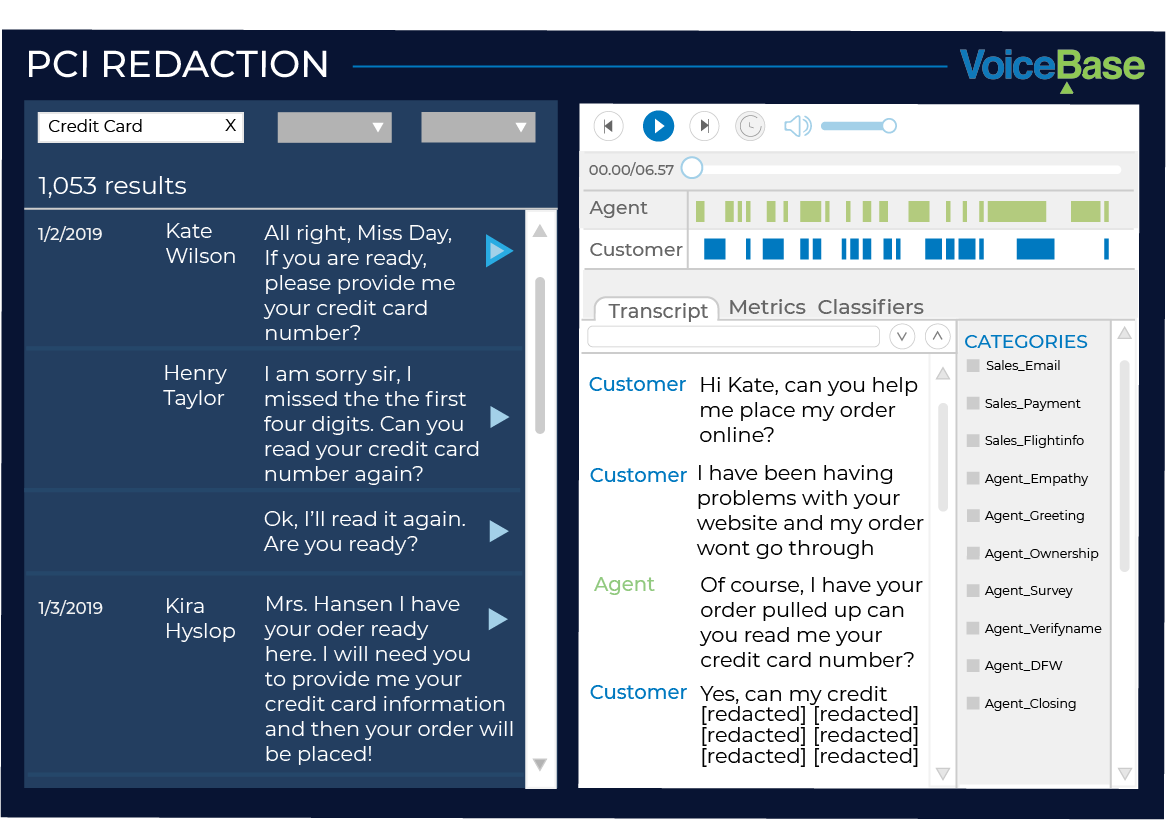
VoiceBase automatically detects and then redacts PCI (Payment Card Industry) data from your call recordings using a highly accurate speech recognition engine and proprietary machine learning algorithms. Using VoiceBase’s PCI Call Redaction and Detection, you can easily query and share your call recordings to unveil rich customer insights without breaching PCI compliance standards. There is no additional lift or time increase for agents or managers.
VoiceBase’s automated AI-Powered redaction technology eliminates the risk of human error from the process and provides a streamlined PCI compliance solution where data is not stored as per the PCI requirements.
It works in the background using Natural Language Processing (NLP) to efficiently detect, redact, and remove all PCI data from call recordings, transcripts, and conversations. This means that all operations depending on the rich data within customer conversations can still fully function without the risk of exposing sensitive data. The credit card data is automatically scrubbed from recording and replaced with a white tone. VoiceBase returns scrubbed recording and the transcript with data removed for users.
DATA REDACTION BRINGS HIGH ROI FOR ADOPTERS
Money is the major motivation for hackers. Verizon Data Breach Investigation report demonstrates that financial gains is the primary motivation for hackers and fraudsters with more than 60%.
Illegally obtained data is sold on the dark web and financial data is in high demand on the dark-web: accounting for 8% of all activities. 50,000 login credentials to Bank of America accounts are on sale.
Implementing data redaction technology can bring a high ROI. To demonstrate this, we will present a hypothetical case in which 1,000 call recordings are hacked and hackers obtained sensitive financial data.
Revenue calculation for hackers:
According to a Semafone Survey, almost 70% of call center agents ask customers to read their sensitive information out loud so data such as credit card information is also included in call recording and transcribed.
Credit card numbers alone can be as much as $20 according to a Symantec report. The average price for a single credit card number is $12. As more data such as billing information, CVC code, and login details are included in the hacker’s offer, the price increases significantly, being purchased at as high as $45.
Source: https://blogbyrainer.files.wordpress.com/2019/02/symantec-internet-security-threat-report-2019.pdf
In this example, we will calculate the price of a single credit card number as $12.
Since sensitive information such as credit card details are read out loud in approximately 70 out of 100 calls made to call centers, 1,000 voice recordings would bring approximately 700 credit card numbers to hackers. This quickly turns into $840,000 revenue from sales on the dark web.
Average call duration at call centers: 5.97 minutes
Calculating costs for hackers per call
1,000 call recordings were stolen. Hackers have to follow a set of steps to extract card information and sell it on the dark market. This process consists of the following steps and each step imposes additional costs.
For 1,000 calls, the cost will be as follows:
- Transcription of a call to text: Speech recognition software provided by Google and Amazon can be used to transcribe the content of calls. Google, for example, charges $0.006 per 15 seconds. 1,000 calls amount to 6,000 minutes of call on average. $144 would be the cost of transcription for 1,000 call recordings.
- Validation of card number: Credit card numbers can be validated for free on various websites.
- Human quality review: While speech-to-text software significantly accelerates the process and brings down transcription cost, the accuracy is still lagging behind that of humans: The current error rate for commercial speech-to-text software products is estimated to be around 12%, 3 times less successful than humans. Therefore, human assessment is needed to guarantee that all 16 digits in a credit card number are captured correctly.
Credit card numbers are pronounced in a detectable interval so these intervals can be separated and sent to human reviewers for quality control.
- Thirty seconds is a reasonable time interval for credit cards.
- Hackers can find human reviewers on platforms such as Mechanical Turk.
- Since there will be 30-seconds snippets from each cell, the reviewer will assess the quality of 120 calls per hour.
- In transcription, the charge per minute starts at $0.80 cents. The cost of a 1-hour audio will be $45.
- The transcription quality control price per 1,000 calls will be $375.
Total revenue from Hacking Of 1,000 Call Recordings: $8,400
Total Cost to Hackers: $144+$375=$519
Profit Margin: 93%
Profit Per 1,000 Calls: $7,881
As can be seen, hackers would operate on 93% profit margin and make as much as $7,881 from hacking 1,000 call recordings. Huge profit margin provides the incentive for hackers to target call centers.
HOW VOICEBASE DATA REDACTION TECHNOLOGY CAN ELIMINATE HACKER’S ROI ON STEALING CALL RECORDINGS
The more sensitive data hackers obtain, the higher the profit margins they operate on. Considering that their main incentive is financial gains, reducing or eliminating hackers’ high ROI can improve security and prevent threats to call recordings data.
VoiceBase’s sensitive data redaction technology can help make hackers’ business unprofitable in terms of call recordings. VoiceBase’s sensitive data redaction technology is capable of detecting the time interval in which sensitive PCI data such as CVC code and credit card number are spoken out loud. It redacts such data before it is stored on databases embedded in the content of call recordings. It scrubs actual call recordings and replaces sensitive data on transcripts with the term [REDACTED].
VoiceBase technology works at 99.7% accuracy. If 1,000 call recordings contain PCI information, sensitive information will be immediately redacted from 997 call recordings.
In the above hypothetical example, 700 call recordings contained a sensitive credit card number and this brought $7,881 of profit to hackers. With VoiceBase’s data redaction technology, only 2 or 3 of those calls would give hackers access to the credit card number.
Considering that the cost would remain the same, $519, and revenue from sale of credit card information down to $24-$36, the hackers will incur losses.
This will significantly eliminate hackers’ financial gains and repel them from seeking ways to illegally obtain call recordings.
ROI FOR ORGANIZATIONS IN ADOPTING VOICEBASE’S REDACTION TECHNOLOGY
Cost of a breach
IBM Cost of A Data Breach Report reveals that the impacted business incurs $150 loss per each customer record when a breach occurs.
For the hacking of call recordings by hackers, this cost per record can include the following:
- PCI non-compliance fine: Non-compliance with PCI Rules subject merchants to fines worth $25 per the card leaked. The size of business and degree and volume of violation also play a role in the calculation of fines.
- Loss of business due to abandoning customers: Ponemon Institute’s research demonstrates that 36% of loss due to a data breach can be traced back to a loss of business due to the erosion of customer trust.
- Compensation to customers due to breach: Customers usually suffer financial consequences due to stolen data such as social security numbers and credit card information.
- Fines due to breach of privacy and banking regulations: Sensitive data included in call recordings such as credit card details and even previous purchases are considered as personally identifiable information under global privacy laws such as GDPR. Businesses may face administrative fines based on these laws.
If 1,000 call recordings are hacked, as in the above example, 700 of them will contain PCI and other sensitive information.
A breach of 700 records would result in $105,000.00 loss for the business. Dividing by the total number of the call, which is 1,000, the cost per call can be calculated as $105.
How does VoiceBase’s data redaction technology bring high ROI for organizations?
Implementing sensitive data redaction technology has high ROI for merchants.
VoiceBase’s data redaction technology powered by artificial intelligence costs $0.01 per minute so the price per average 6-minute call is $0.06. By just incurring $0.06 per call, a business can shield 99.7% of all call recordings from external attacks.
Returning to our hypothetical case, only 2 or 3 call recordings will be stolen compared to 700 thanks to VoiceBase’s A.I powered redaction technology so the total cost will only be around 2*$150=$300 instead of $105,000.00.
By just incurring $0.06 per call, a business can shield 99.7% of all call recordings from external attacks.
REDACTION VS OTHER TECHNOLOGIES
There are other technologies to protect sensitive data other than the redaction technique. These can be a substitute to redaction or used complimentary with redaction.
Encryption: Encryption is the conversion of original plaintext data into an unreadable format so that unauthorized parties cannot unlock the original content. Encryption does not prevent authorized users from accessing, downloading, and leaking data so call center agents may access call recordings, upload them into portable devices and share if they hold a decryption key.
Redaction, on the other hand, is more flexible because only sensitive data is stripped from records so even if agents access the call recordings, they cannot misuse it.
Stop/Start system: When a customer starts reading his/her payment details out loud, the recording pauses immediately until the customer finishes it.
Manual stop/start proved ineffective because call center agents occasionally miss doing that and end up recording the sensitive data. Once sensitive data such as CVC code is stored, even by accident, the organization falls non-compliant with PCI standards as sensitive data should never be recorded. This leads to fines.
Why redaction is more effective:
Once sensitive data is stored and spread across different databases, laptops, and other documents, it is extremely hard to ensure its security and discover and erase it if need be in the future.
Redaction eliminates this problem because it detects and strips off data before even storage so that there will be no concern regarding the security and integrity of data.
HOW REDACTION CAN REDUCE RISKS RELATED TO INSIDER THREATS
Security incidents caused by inside actors rose by 47% this year and call center agents’ access to the content of call recordings is one of the biggest threats.
While certain organizational measures can be taken such as CCTV monitoring and banning of pen& paper to prevent taking notes, preventing sensitive data from becoming part of the call center environment is the most effective method.
Insider threat is not limited to the agent listening to the call but can occur for any employee with access to call recordings. 30% of call center agents already report that they can access sensitive customer information which is on file even without a call with customers.
If an agent gains access to servers where call recording files are stored, he/she can then upload those files on a personal device and may be tempted to make a profit.
Even if the call recordings files are encrypted, agents may somehow obtain the decryption key to unlock the content of calls and illegally sell it on the dark web.
The most effective method to prevent insider attacks is to not hold call recordings at the call center and not record sensitive data in the first place. By employing automated redaction technology, you will not store sensitive data so that your employees are also incapable of accessing sensitive data and steal it.
CONCLUSION
Call Centers are a crucial hub where sensitive information is exposed to both external and internal threats. Names, social security numbers and bank account details are contained in call recordings and cybercriminals and fraudsters are particularly interested in such data for malicious purposes such as selling them on the dark web and doing account-take-over and transfer money.
PCI standards prohibit the holding of sensitive authentication data and require stringent security measures for cardholder data. Furthermore, privacy laws such as GDPR apply to sensitive data contained in call recordings.
To mitigate security risks and achieve compliance with those complex rules, sensitive data redaction technology should be implemented.
Download the Executive Guide to Call Center Compliance: